Imprivata Mobile Access Management has deep integration with Microsoft Intune. The instructions below describe how to set up MAM to use Microsoft Graph APIs. Optionally, you may add an Enrollment Profile for touch-free enrollments of non-DEP devices.
To configure the Imprivata Locker Android app with Intune’s Managed Home Screen, see this article.
API Integration
Microsoft API Integration is recommended for both DEP and non-DEP enrollments. API integration adds additional features to customize your workflows, including device delete, device sync, and clear passcode.
There is a one-time process to allow Mobile Access Management access to your Intune tenant. First, your Azure administrator must create a new App Registration within Azure. Then your MAM administrator will add the Azure OAuth credentials to MAM.
Determine the Permissions Model for the Authentication Method
Depending on your environment’s needs, you can use one of the following permissions models as the authentication method for MAM.
- Application permissions – Imprivata Locker runs in the background without a signed-in user. See Option 1: Application Permissions.
- Resource Owner permissions – the authentication method for delegated permissions. The resource owner authorizes Imprivata Locker to access the resource on its behalf. Supported in MAM 7.2 UAT and later. See Option 2: Resource Owner Permissions.
Step 1: Microsoft Azure Setup
1. Log into your Azure tenant at portal.azure.com.
2. Search for the service App registrations.

3. Create a new registration.
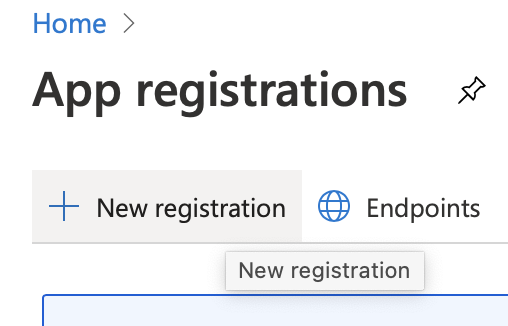
4. Name the application “MAM API Access” or something similar.
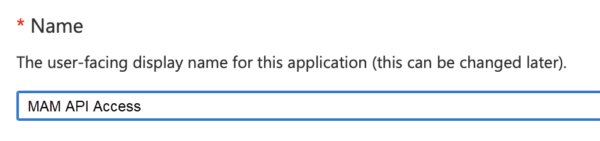
5. Choose Accounts in this organization directory only from the list of supported account types.

6. Leave the Redirect URI blank.
7. Click OK to create the application. The application is created.
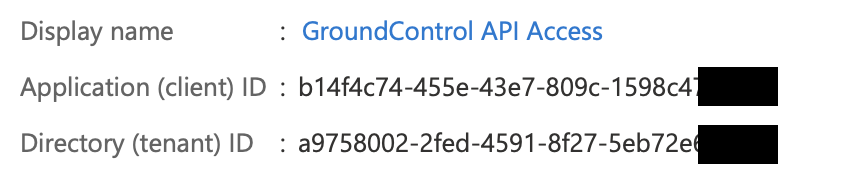
After registering a new application, you can find the application (client) ID and Directory (tenant) ID from the overview menu option.
Copy both the Application (client) ID and the Directory (tenant) IDs to a safe place. You will use these in the MAM Admin console in a later step.
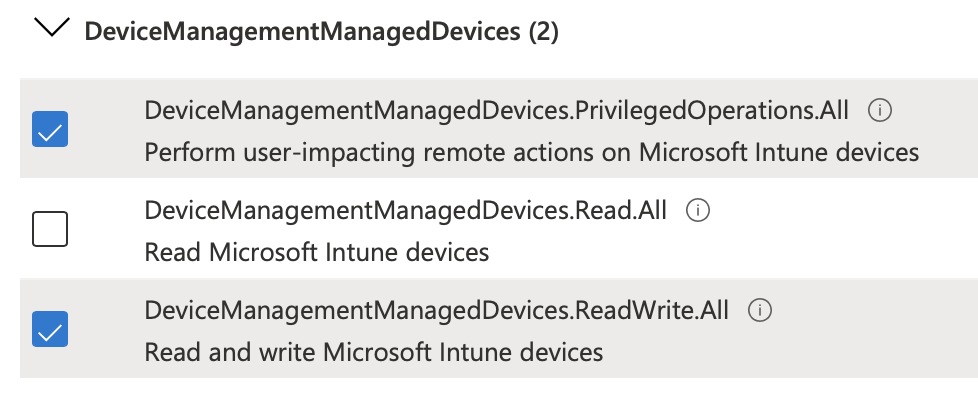
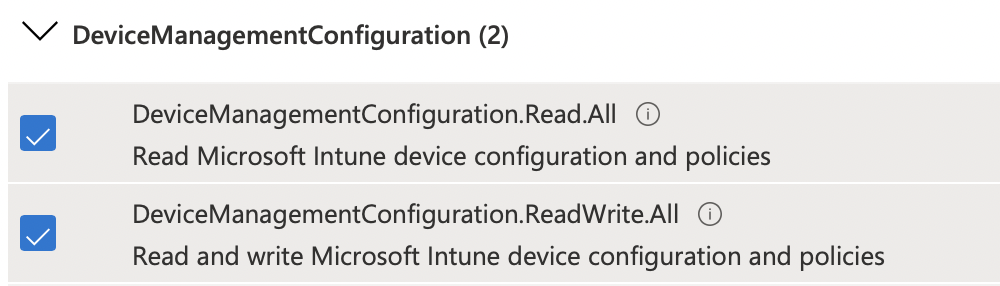
8. In the vertical navigation bar, select API permissions.
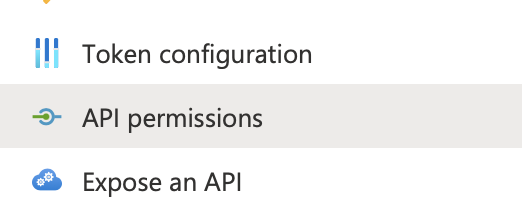
9. Select the Microsoft Graph API.
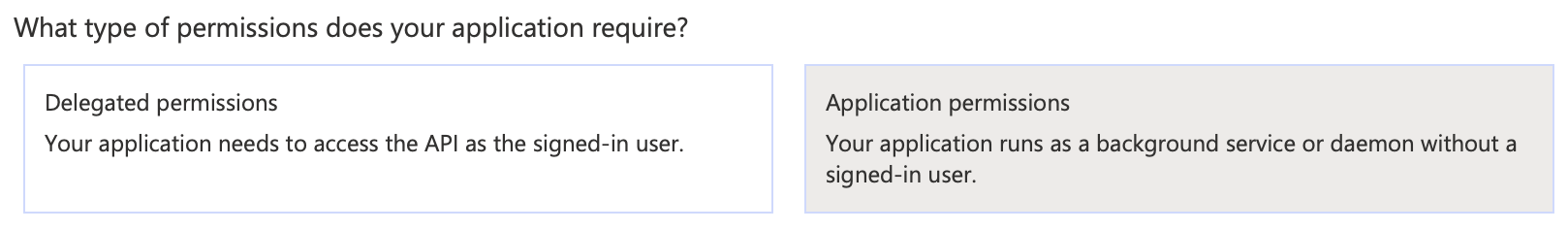
At this point, you must decide which permissions to use: Application or Resource Owner.
Step 2: Mobile Access Management Setup
- In the MAM Admin console, navigate to Admin > MDMs.
- To add a new MDM, click Add and select Intune.
- Type a descriptive name in the MDM Name box.
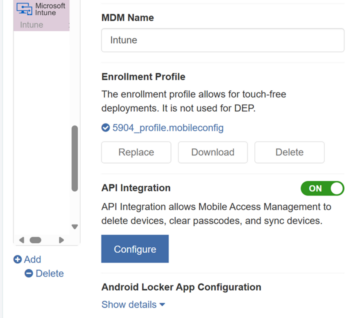
- Skip the enrollment profile.
- Switch API Integration to ON and click Configure.
- In the Microsoft Intune API dialog, configure the following information:
- In the Use delegated permissions, select one of the options as the authentication method: Application or Resource Owner.
- In the Client ID box, type the Client ID of your Intune environment.
- If you selected Application as the authentication method for delegated permissions, in the Client Secret box, type the client secret you saved earlier.
- If you selected Resource Owner as the authentication method for delegated permissions, type the Resource Owner Username and Resource Owner Password.
- In the Tenant ID box, type the tenant ID you saved earlier.
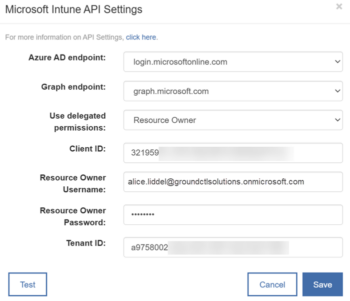
- Click Test to verify connectivity.